DATA SECURITY & COMPLIANCE | 10 MIN READ
What is P2PE?
How Point-To-Point Encryption Solves PCI-Compliance Concerns


What is Point-To-Point Encryption?
Each device is individually injected with an encryption key unique to the merchant. This carefully-controlled process takes place off-site at an approved Hardware Security Module (HSM). Once completed, these PCI-certified devices are then securely shipped to the merchant.
What's the benefit of using a P2PE device?
Once card data is keyed into a merchant's computer, the company's whole network becomes “in scope” for PCI auditing and compliance standards. As PCI compliance guidelines and requirements become more complex and costly, P2PE devices offer a quick and relatively inexpensive solution.
P2PE solves PCI compliance issues because cardholder data is keyed directly into the device, where it's encryped before ever hitting the merchant's computer, network, or servers.
“Our solution prevents clear-text cardholder data from ever being present in our clients' network. That means their customer's credit card data isn't accessible in the event of a data breach. This also removes our clients computers and servers out of scope for PCI compliance.
Jeff Mains
CEO, Intelligent Contacts
Our PCI-Certified P2PE devices undergo the most extensive security measures?
Once the unique encryption key has been injected, our certified devicesare designed to detect tampering. If malicious activity is detected, the device is automatically deactivated, preventing a breach.
“While there are other providers offering solutions as “end-to-end encryption solutions,” most are non-validated P2PE products. Only P2PE solutions listed on the PCI-SS website have been audited and approved by the Payment Card Industry Council.”
Jeff Mains
CEO, Intelligent Contacts
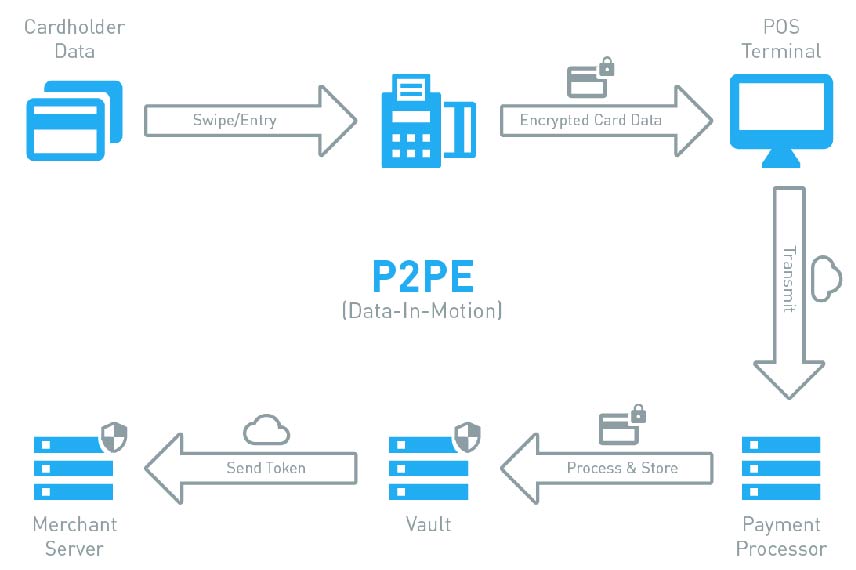
How our P2PE solutions reduce PCI compliance requirements
Our PCI-approved P2PE devices are fully-integrated with our merchant gateway and virtual terminal. All transactions can be managed and reconciled in one place, or sent to your system of record (collection software, EHR, CRM) through our Rest API or sFTP.
Looking to solve yearly PCI compliance headaches with one call! We can help!
Resources
More Articles Related Consumer Payments
Why Your Contact Center Numbers Keep Getting Flagged as Spam, and What to Do About It in 2026
The Shift Splitting Split Market Leaders From Legacy Players in 2026
How Virtual Negotiation Increases Payment Rates: The Psychology Behind Letting Customers Set Their Own Terms
The Shift Splitting Split Market Leaders From Legacy Players in 2026
5 Ways AI Agents Are Quietly Revolutionizing Client Satisfaction
The Shift Splitting Split Market Leaders From Legacy Players in 2026



