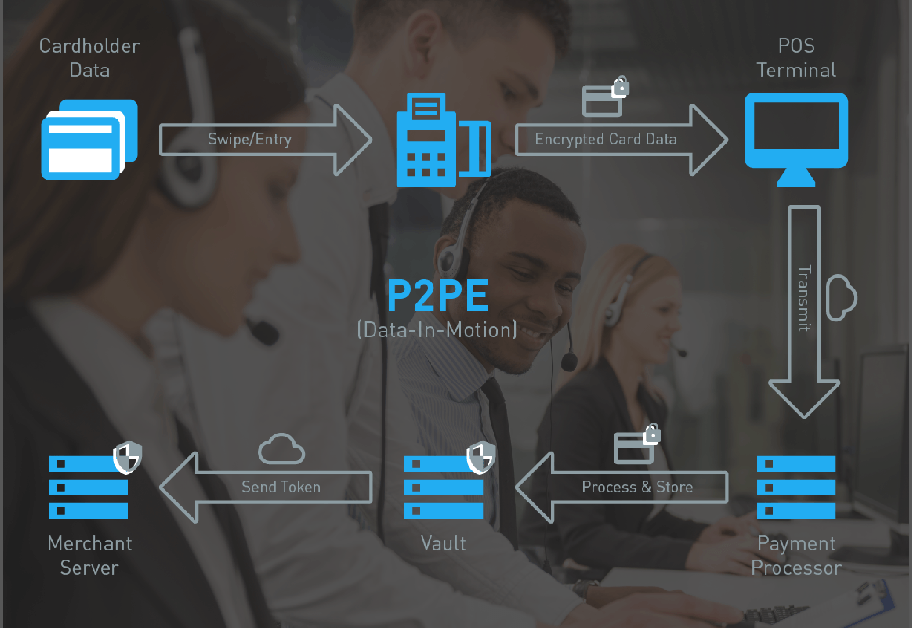
P2PE – Point to Point Encryption
Instantly make your office 100% PCI compliant with our fully-integrated payment gateway & P2PE Point to Point Encyption devices.
PCI-Certified Devices | Point of Service | Card Not Present
PCI Certified
Protect Against Malware
Encrypt Data
Reduce PCI Scope
What is P2PE?
P2PE devices are PCI-validated technology that can take your business network out of scope for a PCI audit and protect your customer's credit card data.
PCI certified P2PE devices are made for security, designed to detect tampering, and abide by strict controls to protect encryption keys. When you implement a PCI certified P2PE solution like ours, you get a 90% drop in PCI requirements. Instantly.
U.S. data breaches in 2016
Records exposed
Lost per record

Be On Guard.
PCI certified P2PE devices are made for security and designed to detect tampering. If malicious activity is detected, the device is automatically deactivated, preventing a breach at the point of entry (also called point-of-interaction, or POI) device.
Encryption Is Key.

Shrink Your Scope.
P2PE Features
Manage:
Users, Partners, Clients, Locations
Devices:
Device Deployment, Activation, Termination (end of life)
History:
Transactional, Device, User History
Reports:
Management, Device, Shipment, Transactional Reports, Easy Export/Download